SPY EYE is a Network Surveillance software. It performs 28 different functions and is still in the evolution stage.
Technical Specifications
It is completely built using JAVA.
Multitasking enabled with 44 java threads.
Total number of Java classes: 35 for easy and proper understand ability of code.
Total Lines of code: 8346.
Requirements
It needs JVM (JAVA Virtual Machine).
It needs JMF (Java Media Framework).
LAN connection.
Internet connection.
45 MB free space in RAM for proper functioning.
Operating System : Windows 98/XP/VISTA
It is specially designed to be operated inside the IIITB hostel but it can be operated anywhere according to the need of the user.
The basic requirement of the software is that the computer on which it is running should be connected to the network or simply LAN because out of 28 features some of them are totally dependent upon LAN.
If suppose LAN is not present and only Internet connection is present then also some features can be executed.
If suppose neither LAN nor Internet is present then in that case also there are some features that can still be executed without any problem.
So the basic requirement for this software to be used is that you must have a computer.

Features:

SCAN:
Using this feature we can scan whole IITB hostel (Boys Hostel (MH1 & MH2) and Girls Hostel) network and see who is currently online or offline. The students whose name appears green in color means that they are online and the students whose name appears red means that the are offline. Online here menas that they are currently connected to the LAN(Local Area Network).
Whenever SCAN button is pressed the current time is printed in front of the start time label and whenever the scanning process end, the end time is displayed. Now coming to some internal details, this scan functionality was previously implemented using only single java thread, at that time the whole scan process was taking approx. 30 minutes but when it is implemented using 12 java threads the total time reduced to approx. 3 minutes i.e. 1.08 seconds for each computer(total 119 computers).
When the scanning process completes, it shows a message for confirmation from the user.

TRACE ROUTE:
This is another feature which is used for tracing the route to any particular server in the world. Whenever the start tracing button is clicked, the tracing start right from the default gateway and goes on until the destination is reached. The destination server name or IP address is specified by the user in the text box. As the packet hops from one server/router to another srever/router, all details with time in milli secs is displayed on the screen. Suppose the destination server is “www.google.com” then the final hop goes to the location in Mountain View, California, US where actual google server is located.

SYSTEM:
This is used for obtaining the system information. It shows details like number of cores in the processor, name of operating system, version of operating system, number of partitions in the HDD, Used memory, free memory related to each partition. Memory usage of JVM(Java Virtual Machine). A separate dedicated thread is used to get the current memory allocated to the JVM. It aslo shows the maximum amount of memory that can be allocated to JVM by that Operating System.

SERVER CLUSTER:
This is another functionality which is used to find out the number of servers that are behind the loadbalancer server which actually balances the load across several servers in the cluster and redirects each incoming request to any server in the cluster by following some algorithm for e.g round robin fashion.

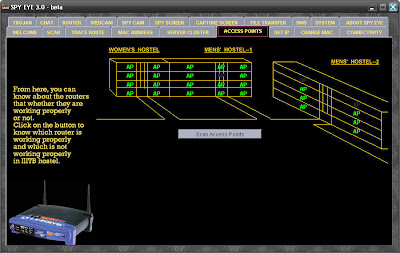
ACCESS POINTS:
This is another utility which is used to get the status of all the wireless routers that are present in the IIITB hostel(both boys and girls). All the access points that are currently availabe and working properly appears green in color.
MAC ADDRESS:
Using this you can retrieve all your MAC addresses related to your own computer system. It will show a list of MAC addresses that are associated to your system. Suppose you have Wired LAN and Wireless LAN then it will show both the MAC addresses with each specific device name. This can be simply done by just clicking on the button “Retrieve my MAC Address(es)”. Apart from all these you can also know the MAC address of your friends’s system. But the condition is that both the computer should be in the same network. To know your friend’s MAC address, simply enter the IP address of his computer in the text box and then press the “Retrieve MAC address” button. You will get the MAC address. You can do a lot of illegal things with this MAC address.

GET IP:
From here you can do to things related to IP addresses (Internet Protocol Address). Firstly you can know the IP address of any server or any website in the world. To do this just simply type the URL (Uniform Resource Locator) address of the website and press the “Find IP” button.
To know the IP address of own system simply press the button “GET MY IP ADDRESS”. As a result a popup message will appear showing your system’s IP address.

CHANGE MAC:
This feature is currently blocked because you can do a lot of illegal things by changing the MAC address. From this software we can easily get another’s MAC address and suppose if we change our MAC address to some other’s MAC address then whatever you do from your computer for eg. Huge download then you will not be caught but the person whose MAC address you are using will be caught. That’s why this feature has been blocked.

CONNECTIVITY:
From here you can check the connectivity of your system with the outer world. It shows whether you are connected to the LAN or INTERNET. To know the Internet connectivity, simply press the button “Internet Connectivity”. A popup message box will tell your connectivity.
To know the LAN connectivity, simply press the button “LAN Connectivity”, again a popup message will appear showing the LAN connectivity.

TROJAN:
Using this feature you can trace the TROJAN viruses. To do this, simply click on the button “Scan Ports”. On pressing this button, a list of all the active connections and processes using the internet connection will be displayed. Now seeing this, you can easily identify whether you are infected with Trojan viruses or not. You can also infect your computer with a harmless computer by clicking on the button “Infect with TROJAN”. Later on you can delete this TROJAN by clicking the button “Delete TROJAN”.

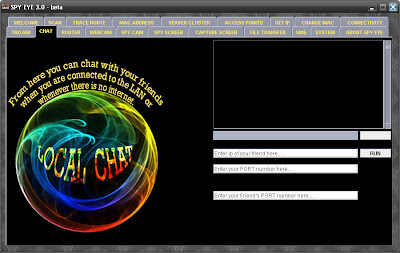
CHAT:
Using this feature you can CHAT locally with your friend. This feature is useful whenever there is no Internet present or whenever you are unable to access google talk or google chat. To use this feature, you have to enter the following information:
IP Address of your friend.
PORT Number of your fiend’s computer.
Enter your own PORT Number.
After filling these details, you have to press “RUN” button.
After this you can send the message by clicking on “the SEND” button.
ROUTER:
Using this feature, you can see the details stored in cache memory of the Router to which your system is connected. To see the details, click on the button “View Router’s Cache”.
You will basically see all the MAC addresses associated with the machines that are currently using the router. This works well with Wireless Router or Wireless Access Points. In order to delete all the entries in the cache memory of the router, simply press the button “Delete Router’s Cache”.
In some routers this feature is not available.

WEB CAM:
If your computer is web cam enabled (Inbuilt webcam or External webcam), you can use this feature. Apart from JVM you should also have JMF installed on your system. Click on the button “VIEW YOUR WEBCAM” to start viewing your webcam. You can pause or resume the webcam streaming. You can also take snap shot from your webcam by clicking the button “TAKE SNAPSHOT”.

SPY CAM:
Using this feature you can get the images directly from the webcam of your friend’s computer without informing him about this spying. To do this, enter the IP address of your friend’s computer in the text box and click on the button “Get Remote Spy Cam Snapshot” The image will then be saved in current folder in which SPY EYE 3.0 is located. This feature can be used in small companies for tracking their employees that whether they are on their seats or not or even somebody else is sitting on the seat.

SPY SCREEN:
Using this you can see what your friend is doing in his laptop at any instant of time. You can get the whole screenshot of the screen by entering the IP address of your friend’s computer and then clicking the button “Get Remote Screen Shot” Again the image will be saved in the home folder i.e. folder containing the SPY EYE 3.0. You can actually know whether your friend is telling the lie or truth that whether last night he was actually studying or watching movie.

CAPTURE SCREEN:
Using this feature you can take the screen shot of your computer’s screen. This feature is similar to the print screen feature of the most common keyboard. But the only difference is that you have to open some program like paintbrush and then save that image. But in this you only have to specify the file name and location.

FILE TRANSFER:
This is useful for local transfer of file between computers that are connected to the same network. To use this, first enter the IP address of your friend’s computer, then browse the file that you want to transfer. The file will be send after selecting the file from the file browse button.
Now suppose if you want to receive file from friend’s computer then simply click on the button “LISTEN FOR INCOMING REQUESTS”. On clicking this button, one dedicated thread will start listening to all the incoming requests from different computers. Now suppose that the file that you want to receive has been received then you can click the button “STOP LISTENING”. Now after clicking this button no more request will come to your computer.

SMS:
Using this feature you can send free SMS to mobile phones using Internet connection. To send free SMS, you must have a way2sms account. There is no need to login to the way2sms website. If you are using low bandwidth internet connection then it is not sure that you will be able to send SMS because this site is always flooded with all sorts of advertisements. It takes a lot of time in opening this site. But using this SPY EYE feature, you can send SMS at the instant of clicking the send button. Simply type way2sms username and password, then type the recipient’s mobile number and message. If you are behind a proxy server then you also have to specify the default gateway, port number, username and password for proxy server.

We presented this software in our technical communication class as a part of technical presentation under the guidance of Revathi Siva Kumar Mam at IIIT Bangalore during summer course.
Team Members:
1. Romil Mehla
2. Sanket Jain
3. Saurabh Goswami
4. Siddharth Anand
5. Zaid
We distributed all the use cases amongst us.
I am grateful to all my team members.
Thanks a lot to all of you................

